
We deliver tools that identify, respond, defend, and avoid digital hazards and vulnerabilities. And our clients have complete control.
We partnered with state of art technological institutions for digital safety and security.
*More details after signed NDA.
Penetration Testing robustness and security of networks and application by carrying out penetration testing and ethical hacking.
Pen Testing is a simulated cyber-attack against your computer system to check for exploitable vulnerabilities.
Expert team is government security checked.

IP Analytic product focuses on big data / mass data extraction, data forensic and cybersecurity specialized on governmental needs. This also includes providing customer tailored trainings and consulting.
Product is based on a government proven, real time data extraction and analytics engine. It offers customers and partners an intuitive, easy to use interface to view and analyze all IP-data transmitted.
Neither software nor hardware can guarantee absolute security, and motivated hackers will always find a way in.
When Deception Technology is used, a break-in attempt is recognized immediately and, above all, the intruder is automatically redirected to an authentic trap.
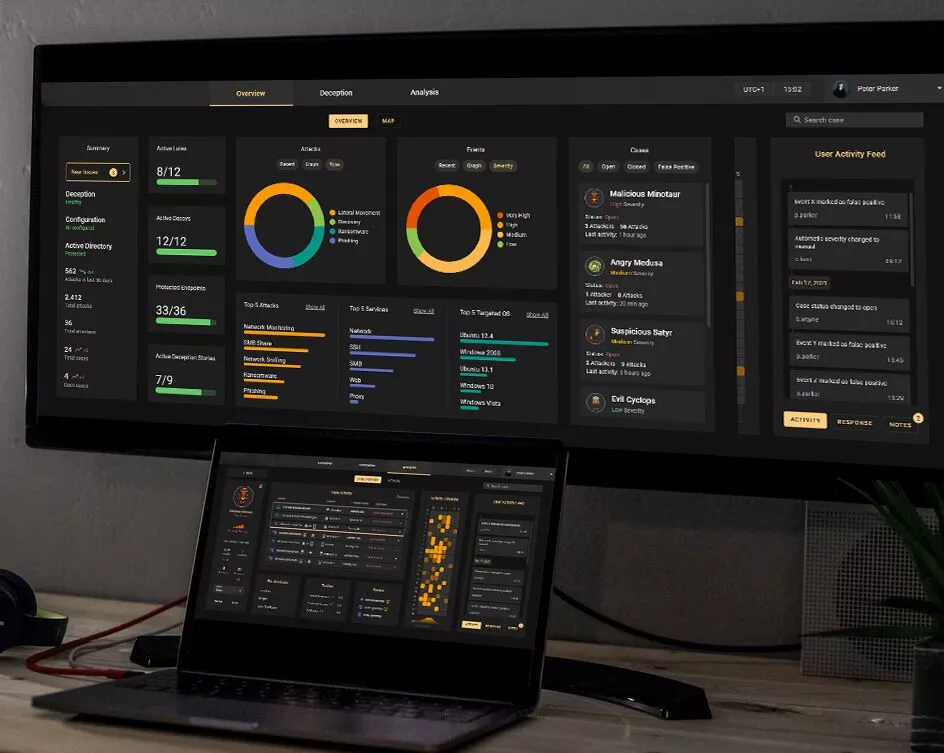
Our team is an assembly of scientists, engineers, inventors and software developers with decades of expertise in building sophisticated platforms, applications, and complex systems in accordance with market trends.

